You can also watch this video on lbry
- Craiglist anonymous email relay system exploited by cybercriminals to propograte their malware
- Malicious excel spreadsheet contained embedded code
- The type of malware is unidentifiable due to a mistake on the part of the bad actors
- Email security company Inky uncovered the campaign
Craigslist's Anonymous Email Relay System
This was the system exploited by the cybercrooks. To respond to an ad on Craigslist you are given a randomly generated email address to get in touch with the seller using.
<a long hex string>@<subdomain>.craigslist.org
Craiglist's email relay system automatically forwards emails received to the seller's true address. This is a relatively simple way of achieving anonymity between seller and buyer without the need for Craigslist to implement their own messaging system.
The Phishing Campaign
A bad actor utilised this email relay system, spamming sellers with phishing emails claiming an ad they had posted had gone against Craigslist's rules. The victims were told they had to fill in and return a form else their account would be deleted.
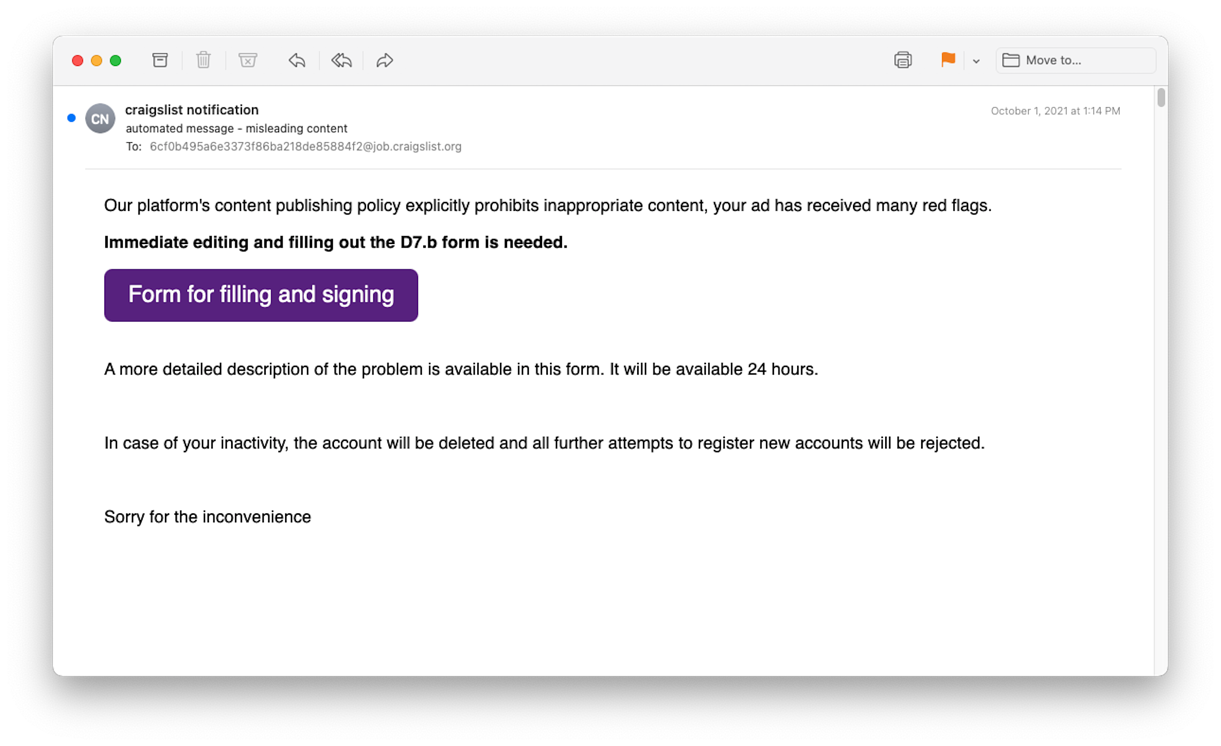
As Inky explains "it appears as if bad actors were able to manipulate the email’s HTML to create that button". The button linked to OneDrive, prompting the victim to download a malicious excel document.
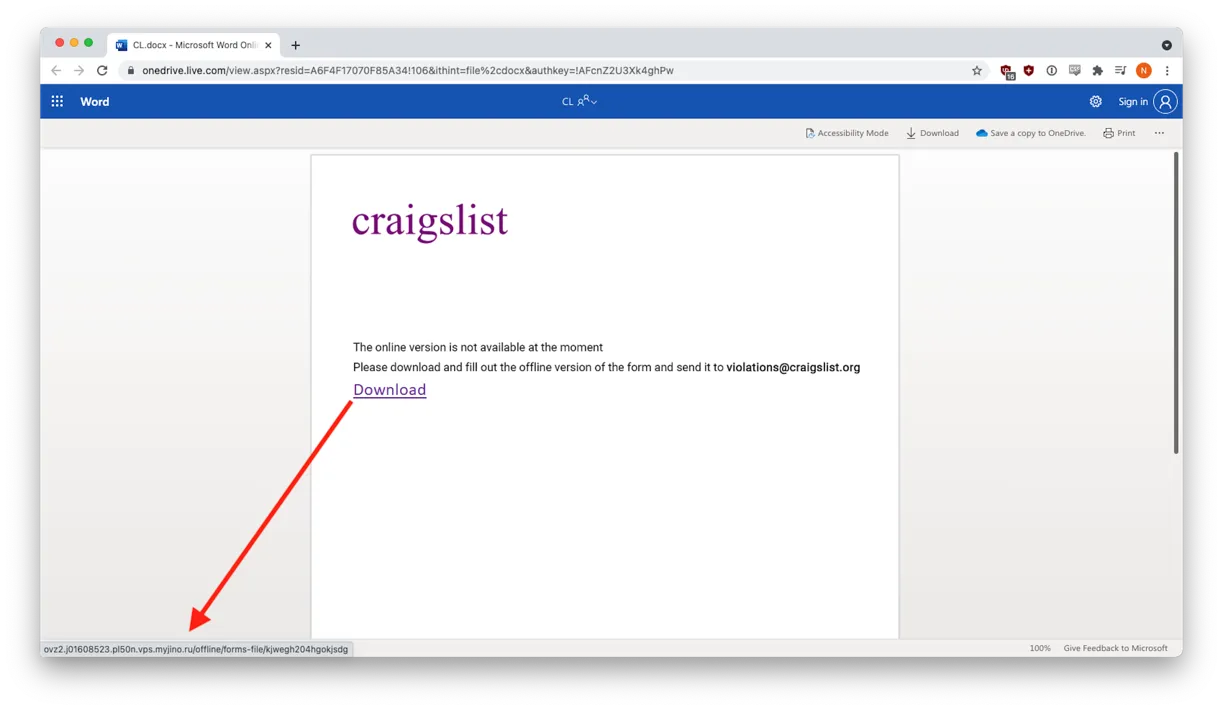
The downloaded document contained a malicious excel macro, which upon execution would communicate with an actor controlled C2 server in an attempt to download further malware.

A 404 error halted any attempt to communicate with the actor controlled server, this was either due to a mistake on the part of the cybercriminals or the content having been removed by the hoster.
A previous video of mine explains how malicious excel documents work: