You can also watch this video on LBRY
- Ransomware originated from the AIDS TROJAN in 1989
- It asked for several hundred dollars to be mailed to a Panamanian PO Box
- The perp avoided trial on mental health grounds
5.2 billion dollars - that’s the total amount of bitcoin payments that have been linked to the top 10 strains of ransomware in 2021 alone.
By the end of the year there will have been over 700 million attempted ransomware attacks, that’s over 1300 attacks every minute or 22 attacks per second, it’s madness. And it’s growing, this year we’re up 150%.
This got me thinking, who or what kicked off this flourishing industry? Who knocked over the first proverbial domino that has led to the absolute state of ransomware in 2021? To explore the first known case of ransomware we have to turn back the clock to 1989.
The AIDS TROJAN
It all began when AIDS researchers started receiving 5 ¼ inch floppy disks in the mail - at the time the AIDS epidemic was peaking.
The floppy disks were accompanied by a set of written instructions.

The program contained within worked as expected, but unbeknownst to the user, malware was dropped on the victim machine, malware known as a “logic bomb”. A logic bomb is malicious code that stays dormant until a certain condition is met.
The condition in this case being 90 reboots - nothing would happen, until the computer has been switched off and on 90 times. On the 90th boot, the user would be locked out of their computer, just like in normal modern ransomware. Victims found themselves staring down the barrel of the world’s first ransomware note.
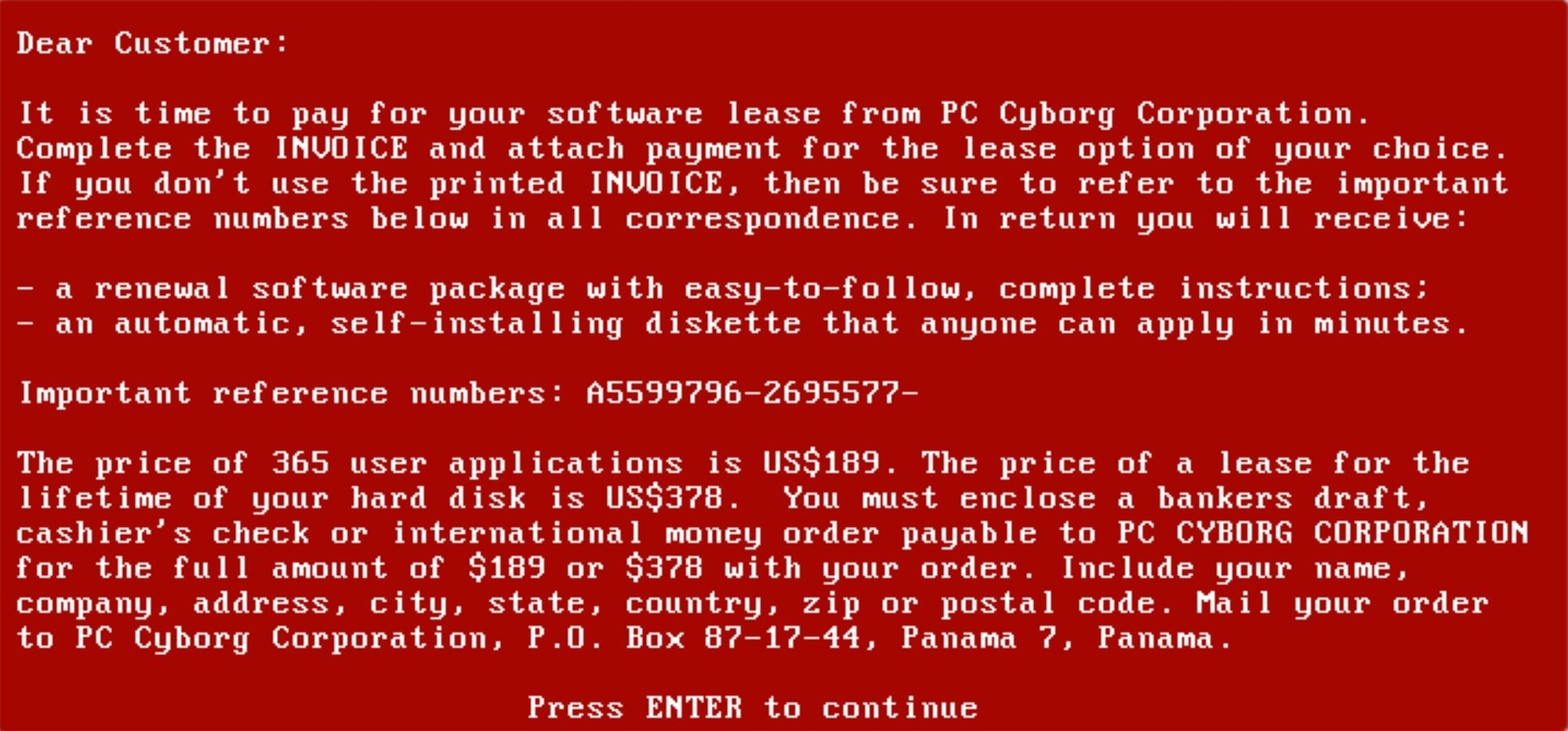
Apart from just preventing the victim from using their PC, the AIDS Trojan also encrypted the names of all the files on the disk and set those files to hidden. This doesn't sound too bad, as only the filenames were encrypted rather than the contents of those files itself, so whilst it was possible to undo the damage if you knew what you were doing, it was also 1989, you couldn’t just google these things. Realistically speaking most victims were kinda screwed.
Whilst modern ransomware almost exclusively asks for ransoms to be paid in cryptocurrency, but this wasn’t an option in 1989, so the malware asks for the next best thing, a cheque! Sent to a Panamanian PO Box - in return the victim would be sent a floppy disk with software to unblock the PC.
The January 1990 issue of Virus Bulletin had a lot to say about this malware, in analysing this malware, the author of the article had no idea he was describing a soon to be multibillion dollar industry when he said “The conception is ingenious and extremely devious”. However, his awe at this creation stops there, “the actual programming is quite untidy”. What follows is what I can only assume is the 1990 equivalent of calling someone a noob, “The programmer was unfamiliar with the capabilities of QuickBASIC 3.0 and not particularly well schooled in general program construction”.
In total, 20 thousand AIDS researchers had received these floppy disks in the mail- quite remarkable when you realise how much an operation like that costs. A floppy disk in 1989 was about $1.5 (an educated guess). 20 Thousand floppy disks would have set you back $30k back then, in today’s money that’s 70k, after you factor in postage it gets even more expensive, and then you’ve got to find the time to package up all those floppy disks. Someone went to great expense and great lengths to do all of this, and to target AIDS researchers? It just doesn’t add up.
Damage
This wasn’t a harmless prank, one of the victims explained in an interview with CNN “The incident created a lot of damage”, “People lost a lot of work” - knowing their computers had been infected, “some scientists pre-emptively deleted valuable data”. “One AIDS organization in Italy lost 10 years of work.”
The Mastermind
As it happens, Panamanian PO Boxes are not immune to traceability. Police hunted down the perp to be one “Joseph Popp”. This wasn’t some kiddo trying to make some quick cash, “Joseph Popp” was an evolutionary biologist, he even got his PHD from Harvard. Not the most archetypal hacker...

Since, no victims were located in the US, he was extradited to the UK to stand trial. Unfortunately I have no definitive answers as to why he made the trojan. The best theory is that he was super salty about being rejected for a job at the WHO. The 20,000 researchers sent the malware came from a list of attendees of the WHO conference in Stockholm a year earlier.
Joseph Popp was never tried for his crimes. There are reports from the time - that he was observed putting curlers in his beard and condoms on his nose in order to ward off radiation, either he had a screw loose, or this was all a ruse to look as crazy as possible to avoid a harsh sentence. Either way, the judge ruled he was mentally unfit to stand trial and he was deported back to America.
We don’t know if anyone actually ended up paying the ransom. But a program to clean up the trojan called “AIDSOUT” was made freely available. Joseph Popp died in 2007, but not before setting up a butterfly conservatory of all things. Regardless, his legacy as the father of ransomware was cemented the day he mailed out that first floppy disk.