You can also watch this video on LBRY
- Two Iranians charged with hacking state voter website, nabbing personal information on voters
- Stolen personal information was subsequently used in a disinformation campaign
- Miscreants posed as proud boys, sending intimidation emails to victims
The Operation
As the recently unsealed indictment explains, new charges have been levied against multiple Iranian individuals for the crime of attempting to “intimidate and influence American voters, and otherwise undermine voter confidence and sow discord, in connection with the 2020 U.S. presidential election.
”The first phase of the Voter Intimidation and Influence Campaign occurred in or about September and October 2020”, when the bad actors attempted to hack “eleven state voter websites”. They failed to hack all but one of their targets, the unlucky website is referred to as belonging to “state-1”. The perps managed to nab tens of thousands of records containing the personal information of voters.
They utilised the emails addresses they had scooped up from phase one, for phase two, sending tens of thousands of fake emails. The emails were spoofed to give the illusion that they were being sent by the proud boys.
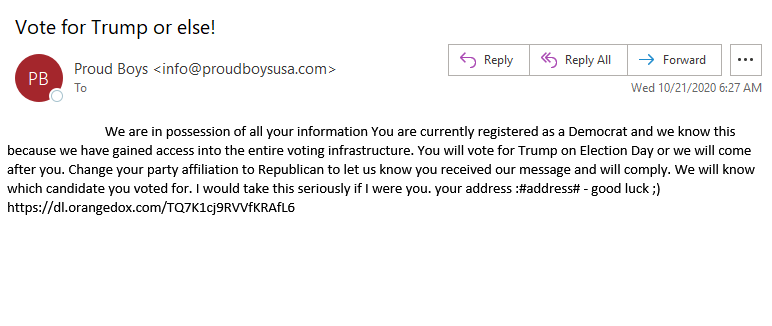
The link at the end of the email downloads a video...
The video is simply a screen recording made using kali linux. The video appears to show "the Proud Boys" hacking into state voter websites and creating false absentee ballots, in reality they’re not… they’ve simulated the intrusion using their own servers. However they have used real user data in this video which they gathered from the first phase of their campaign.
False Flag?
A Reuters article makes some interesting claims which raise the question of whether this may be a false flag. They quote anonymous sources which claim the blurring done by the perps to hide personally identifiable information was lackluster, “snippets of revealing computer code, including file paths, file names and an (IP) address” were visible to investigators.
“Either they made a dumb mistake or wanted to get caught,” said a senior U.S. government official, who asked not to be identified. However this same source went on to say “We are not concerned about this activity being some kind of false flag due to other supporting evidence. This was Iran.”
This video wasn’t just sent to intimidate Democrats, it was also sent to Republicans, claiming “that the Democratic Party was planning to exploit “serious security vulnerabilities” in state voter registration websites”.
The duo accused of these crimes have had a 10 million dollar bounty slapped on their heads, though of course they’re in Iran, presumably, so they won’t be facing a trial any time soon, if ever. The indictment alleges these two worked for an Iranian company “purported to provide cybersecurity services within Iran.” whose clients include the “Iranian government”.